November 2, 2017 Sydney, Australia



November 2, 2017 Sydney, Australia
Licensing of Engineering Professionals: Is there any validity to this practice? The Education Department of the State of New York says — there is. IEEE Policy also says there is. The reality, I have come to continuously over four decades in practice as an electrical power engineer in the service of more than a dozen U.S. firms — is that there is none!

There is an increasing interest in, and implementation of the Internet of Things. As the number and types of interconnections… Read More

In the context of the IEEE Global Initiative for Ethical Considerations in Artificial Intelligence and Autonomous Systems, and with support… Read More

Responsibilities of Scientists and Engineers in Times of Chaos and Upheaval If the future is coming at an ever accelerating… Read More

Pressed for Time: The Acceleration of Life in Digital Capitalism. By Judy Wajcman. Chicago, IL: Univ. of Chicago Press, 2015,… Read More

Dear Editor, Katina Michael, in “Gone Fishing: Breaking with the Biometric Rhythm of Tech-Centricism” (IEEE Technology and Society Magazine, Dec…. Read More

PetaJakarta.org team survey damage along the Ciliwung River using GeoSocial Rapid Assessment Survey Platform (#GRASP) via Twitter, as neighborhood children… Read More

By Gary T. Marx, University of Chicago Press, 2016. Reviewed by Donna L. Halper It goes without saying that we… Read More
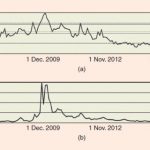
Figure 1. Popularity of the search terms (a) “Stereoscopy” and (b) “3D television” between January 2007 and October 2016, based on… Read More

Rapid advances in science and technology are opening doors for the fulfillment of human desires in ways that were not… Read More

Heather M. Roff and Peter W. Singer [1] strikingly identify a problem for the next American president in the form… Read More

What can parents do? Children need different rules at different ages of development. Here are some 3-6-9-12 Rules for the… Read More

I sat staring at the computer on February 6th, 2006, thinking about the press release I was about to send… Read More

Dear Editor, After receiving my discharge from the United States Marine Corps, the most deplorable fight of my life/career started…. Read More

Having recently relocated to a country where I know very few people, I tried looking for a local branch of… Read More

Minsky (left) was keynote speaker at ISTAS 2013 held at the University of Toronto, Canada. (Right: Steve Mann, ISTAS ’13… Read More

A rugged male Metro Toronto police officer stares down a female protester outside the Toronto G-20 meetings in 2010. She… Read More
Dear Drs. Albrecht and Michael, I recently came across your Editorial titled: “We’ve Got to do Better” [1] and felt… Read More

Guest Blog entry by Cassie Phillips With the recent, record-breaking distributed denial of service (DDoS) attacks carried out with hijacked Internet-of-Things… Read More