Web artificial intelligence (AI) evolution is driven, in part, by the evolution of the web. Daniel Dennett, in his recent… Read More
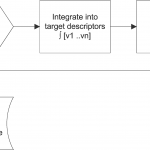


Web artificial intelligence (AI) evolution is driven, in part, by the evolution of the web. Daniel Dennett, in his recent… Read More

By web evolution I’m not talking Internet 4.0, I’m talking Darwinian survival. In the Darwinian model, evolution requires three things:… Read More